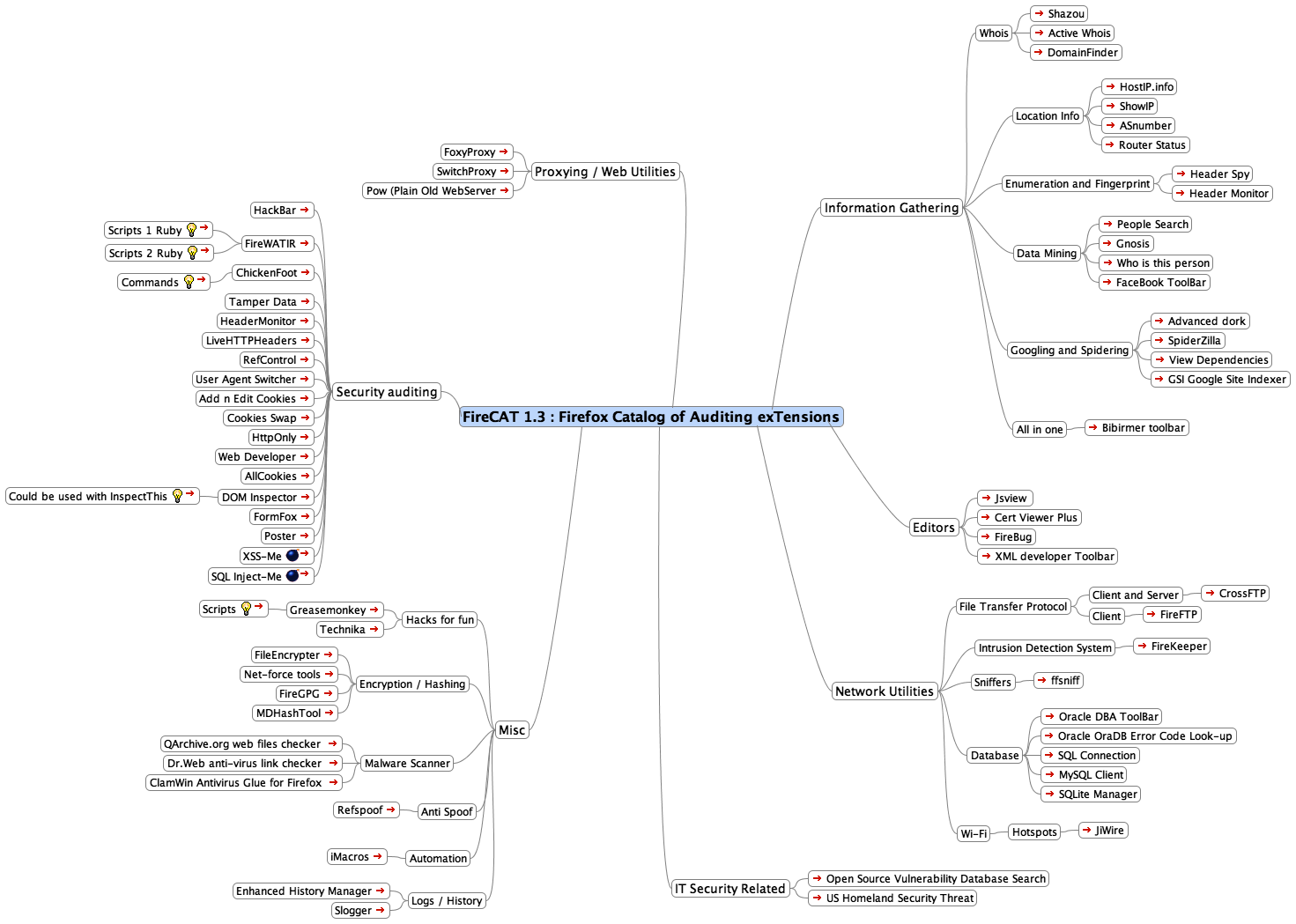
If anybody might have heard about the FireCAT (Firefox Auditing Tools - my favorite) before, then this article will just extract some of the most useful and attainable tools that are must to use while auditing a web application directly through your browser interaction. Following the standard Web Application Pen-Testing methods and those tools provided under FireCAT will evaluate security level of most web applications.
An instant use of FireCAT Tools add a wide range of extensions to your browser to follow-up from Top-to-Bottom to find as much information as possible about your target. Under my experience some of the useful tools are mention below:
Information Gathering
ActiveWhois, DomainFinder, RouterStatus(more useful if you're local/remote network admin), Header Spy, Header Monitor, People Search, Who is this Person, Google Advanced Dorks, SpiderZilla, Google Site Indexer(very useful).
Web Relay/Proxy Auditors
SwitchProxy, FoxyProxy
Security Auditing
Tamper Data(tampering with live web-forms data), LiveHTTPHeaders, User Agent Switcher, Add'n'Edit Cookies, Cookies Swap, AllCookies, DOM Inspector(specifically for developers), Chickenfoot, Poster, XSS-Me and SQL Inject-Me(excellent toolset).
Network Auditing Utilities
FireFTP, FireKeeper(WIDS) ffsniff, Oracle OraDB Error Code Look-up, SQL Connection, MySQL Client, JiWire(Wi-Fi)
Miscellaneous
GreaseMonkey, File Encrypter, Net-force Tools, Refspoof, MDHash Tool, Malware Scanner(Dr.Web), Logs(Enhanced History Manager)
While using any combinition of these tools make a life easier for the Pen-Tester to look for specific vulnerabilities through fuzzing techniques. Although the complete information on extensions available under FireCAT 1.3 release is specified in the screenshot above.
