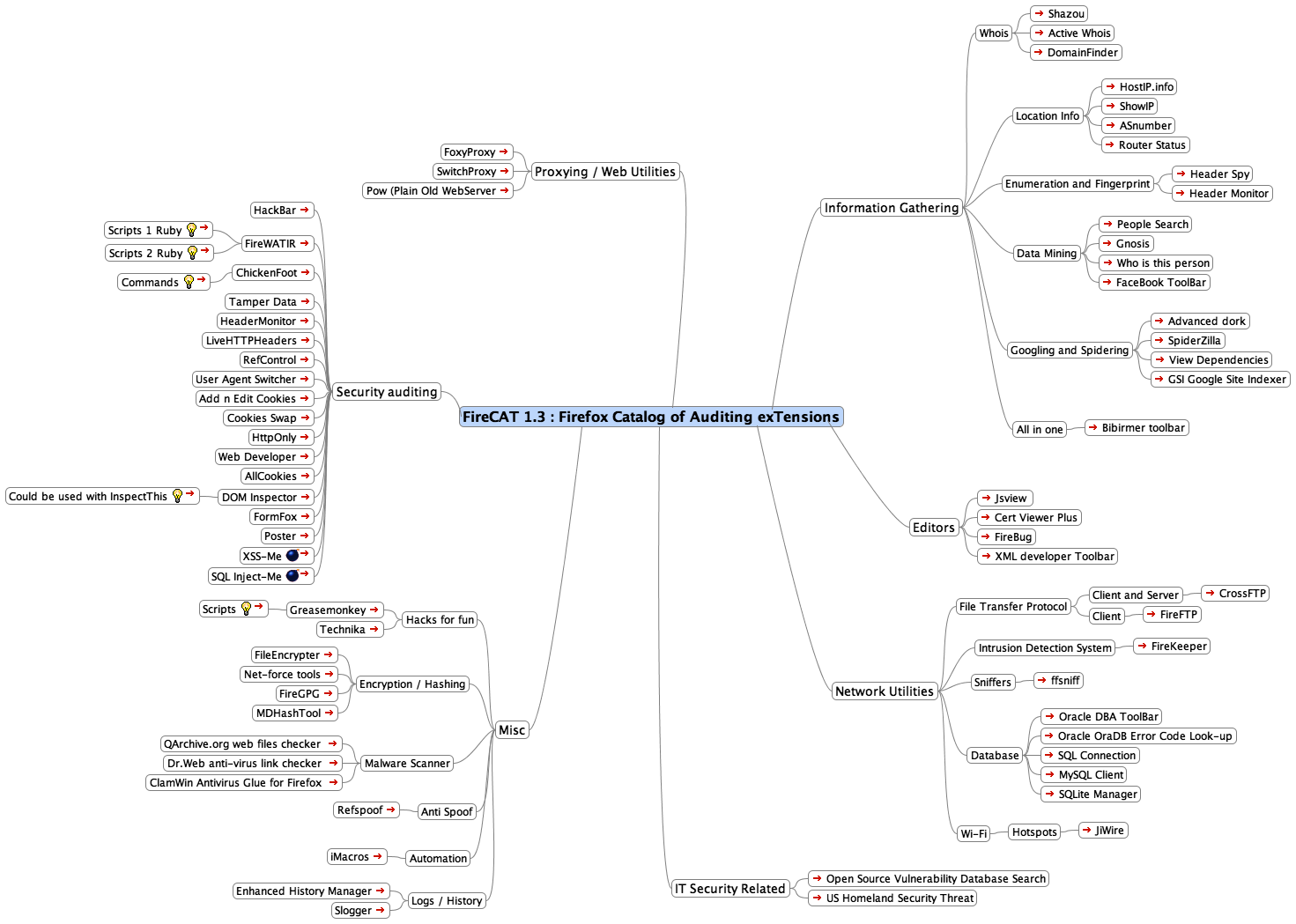
A world of computer forensics has extremely gone under rapid changes for laws and regulations concerning the professionals conducting investigations in day to day basis. Inputting strict jurisdiction for processing the corporate crime investigation has opened new debates in between attackers world (more advanced malicious adversary making it harder to get track down applying anti-forensic techniques) and forensics investigators. As I have mentioned previously to post forensic related tools under their defined categories for the ease of forensics practices. Below is a list of tools that can be used by a forensics examiner during the investigation.
File AnalysisSurfRecon LE rapid image analysis tool
truss
ltrace
xtrace
ktrace
Strings (Download the program strings.exe from http://www.microsoft.com/technet/sysinternals/utilities/Strings.mspx)
Valgrind
Galleta
Pasco (by Foundstone)
Rifiuti
yim2text
InCtrl5
Hachoir
UnxUtils
Cygwin
GnuWin32
P2P Marshal
Disk Analysis ToolsPC-3000
LINReS
SMART (by ASR Data)
Macintosh Forensic Software (BlackBag Technologies, Inc.)
MacForensicsLab
EMail Detective - Forensic Software Tool
EnCase (by Guidance Software) - Most Recommended
Sysinternals Monitoring Tools (Regmon,Filemon and more.)
FBI tool (Nuix Pty Ltd)
Forensic Toolkit (FTK) (by AccessData)
ILook Investigator (Elliot Spencer and U.S. Dept of Treasury)
OnLineDFS
Safeback
X-Ways Forensics
Prodiscover
AFFLIB
Autopsy
foremost
FTimes
Scalpel
Sleuthkit
Zeitline (Forensic timeline editor)
P2 Enterprise Edition (by Paraben)
LiveWire Investigator 2008
Pathways
Metadata Extraction Toolsantiword
catdoc
PuriFile
jhead
laola
vinetto
word2x
wvWare
xpdf
Metadata Assistant
Hachoir-metadata (Hachoir project)
Memory Imaging ToolsFirewire (http://www.storm.net.nz/projects/16)
Tribble PCI Card
CoPilot
Windows Memory Forensic Toolkit (WMFT)
Idetect (Linux)
dd (Linux)
PDA ForensicsParaben PDA Seizure
Paraben PDA Seizure Toolbox
PDD
Cell Phone ForensicsBitPIM
DataPilot Secure View
GSM .XRY
Fernico ZRT
ForensicMobile
MOBILedit
Oxygen PM II
Paraben's Device Seizure
TULP2G
SIM Card ForensicsForensicSIM
SIMCon
Preservation ToolsParaben StrongHold Bag
Paraben StrongHold Tent
Hex Editorsbiew
hexdump
WinHex
Hex Workshop
Forensics Live CDsHelix
SNARL
DEFT Linux
Knoppix STD
Recovery Is Possible - RIP from Tux.org
Stagos FSE
Other Essential ToolsVMware Player
VMware Server
Webtracer
The Onion Router (TOR)
Live View
Parallels VM
Microsoft Virtual PC
Being an excellent investigator it is however extraneous to follow-up beyond these toolset and perform some manual operations on different aspects/dimensions of examination. Keeping in mind those of anti-forensics techniques used by attacker to aid towards hiding their tracks could be more beneficial. As this is a known fact that to prosecute the right person, one should think wisely as of what malicious adversary had done step by step. Remember, in any case you should not modify or alter the original preserved evidence.

En el mundo de la informática forense ocurren cambios muy rápidos debido a las leyes y regulaciones concernientes a la conducta de los profesionales que llevan la investigación día a día. Entrando en la jurisdicción del procesamiento de una investigación del crimen corporativo, se han abierto nuevos debates entre el mundo de los atacantes y el de los investigadores forenses. Como se dijo antes en unos de nuestros post, las herramientas según su categoría para hacer más fácil la practica forense.
Debajo está una lista de las herramientas que se pueden utilizar durante la investigación.
Analisis de archivos:SurfRecon LE
truss
ltrace
xtrace
ktrace
Strings
Valgrind
Galleta
Pasco (by Foundstone)
Rifiuti
yim2text
InCtrl5
Hachoir
UnxUtils
Cygwin
GnuWin32
P2P Marshal
Analisis de Discos:PC-3000
LINReS
SMART (by ASR Data)
Macintosh Forensic Software (BlackBag Technologies, Inc.)
MacForensicsLab
EMail Detective - Forensic Software Tool
EnCase (by Guidance Software) - Most Recommended
Sysinternals Monitoring Tools (Regmon,Filemon and more.)
FBI tool (Nuix Pty Ltd)
Forensic Toolkit (FTK) (by AccessData)
ILook Investigator (Elliot Spencer and U.S. Dept of Treasury)
OnLineDFS
Safeback
X-Ways Forensics
Prodiscover
AFFLIB
Autopsy
foremost
FTimes
Scalpel
Sleuthkit
Zeitline (Forensic timeline editor)
P2 Enterprise Edition (by Paraben)
LiveWire Investigator 2008
Pathways
Extraccion de Metadata:antiword
catdoc
PuriFile
jhead
laola
vinetto
word2x
wvWare
xpdf
Metadata Assistant
Hachoir-metadata (Hachoir project)
Herramientas para crear imagenes de la Memoria:Firewire (http://www.storm.net.nz/projects/16)
Tribble PCI Card
CoPilot
Windows Memory Forensic Toolkit (WMFT)
Idetect (Linux)
dd (Linux)
Herramientas para PDA:Paraben PDA Seizure
Paraben PDA Seizure Toolbox
PDD
Herramientas para celulares:BitPIM
DataPilot Secure View
GSM .XRY
Fernico ZRT
ForensicMobile
MOBILedit
Oxygen PM II
Paraben's Device Seizure
TULP2G
Herramientas para SIM Card:ForensicSIM
SIMCon
Herramientas para Preservacion:Paraben StrongHold Bag
Paraben StrongHold Tent
Editores Hex:biew
hexdump
WinHex
Hex Workshop
Live CDs:Helix
SNARL
DEFT Linux
Knoppix STD
Recovery Is Possible - RIP from Tux.org
Stagos FSE
Y otras herramientas esenciales:VMware Player
VMware Server
Webtracer
The Onion Router (TOR)
Live View
Parallels VM
Microsoft Virtual PC
Debes mantener en mente que existen técnicas anti-forenses utilizadas por los atacantes para ayudar a ocultarse y ser más beneficioso para ellos. Como este es un hecho conocido y para atrapar a la persona correcta uno debe pensar como ella, tratando de recrear paso por paso. Recuerda, en ningún caso debes modificar o alterar la data original.
Traducido por: Rafael, Alfredo, Ali (www.ethical-hacker.net)